- Blog
- /
- Topic
Supply Chain
- All
- Supply Chain Management
- SBOM
- Vulnerability Tracking
- #supplychainsecurity
- Regulatory Requirements
- VEX
- EO14028
- ICS/IoT Upgrade Management
- malware
- ICS
- vulnerability disclosure
- 3rd Party Components
- Partnership
- Press-release
- #S4
- Software Validation
- hacking
- industrial control system
- Code Signing
- Legislation
- chain of trust
- #nvbc2020
- DoD CMMC
- Dragonfly
- Havex
- Log4Shell
- Log4j
- Trojan
- USB
- Uncategorized
- energy
- medical
- password strength
- pharmaceutical
EU Cyber Resilience Act (CRA) Clears Penultimate Step
On December 3rd, the EU's new Cyber Resilience Act (CRA) got a big step closer to being adopted when the European Parliament and the EU Council reached an agreement on the legislation. It...
Continue ReadingA Flurry of Regulatory Action and the Need for SBOMs
Executive Order 14028 on Improving the Nation's Cybersecurity was issued in May of 2021 and provided a roadmap for a series of regulatory initiatives that government agencies (and anyone...
Continue ReadingSorry Blackberry: You Are Part of the Supply Chain
Today, reporters Betsy Woodruff Swan and Eric Geller at Politico published a story: “BlackBerry resisted announcing major flaw in software powering cars, hospital equipment.” They outline...
Continue ReadingNTIA Publishes Minimum Components of an SBOM
In today’s blog post I’d like to recognize all the hard work done by NTIA (National Telecommunications and Information Administration) and congratulate them on publishing the minimum...
Continue ReadingUnpacking EO14028: Improving the Nation's Cybersecurity - Pt. 4
Section 3 - Less Fog, More Cloud Section 3: Modernizing Federal Government Cybersecurity of the Executive Order is all about government agencies moving to the cloud and doing it right. If...
Continue ReadingUnpacking EO14028: Improving the Nation's Cybersecurity - Pt. 3
So you don’t sell to the Feds… Today’s blog is going to take a break from analyzing a specific section of the Executive Order on Improving the Nation’s Cybersecurity and focus on who will...
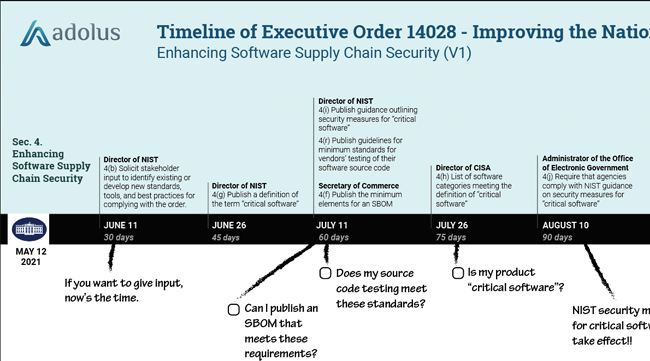
Continue ReadingUnpacking EO14028: Improving the Nation's Cybersecurity - Pt. 2
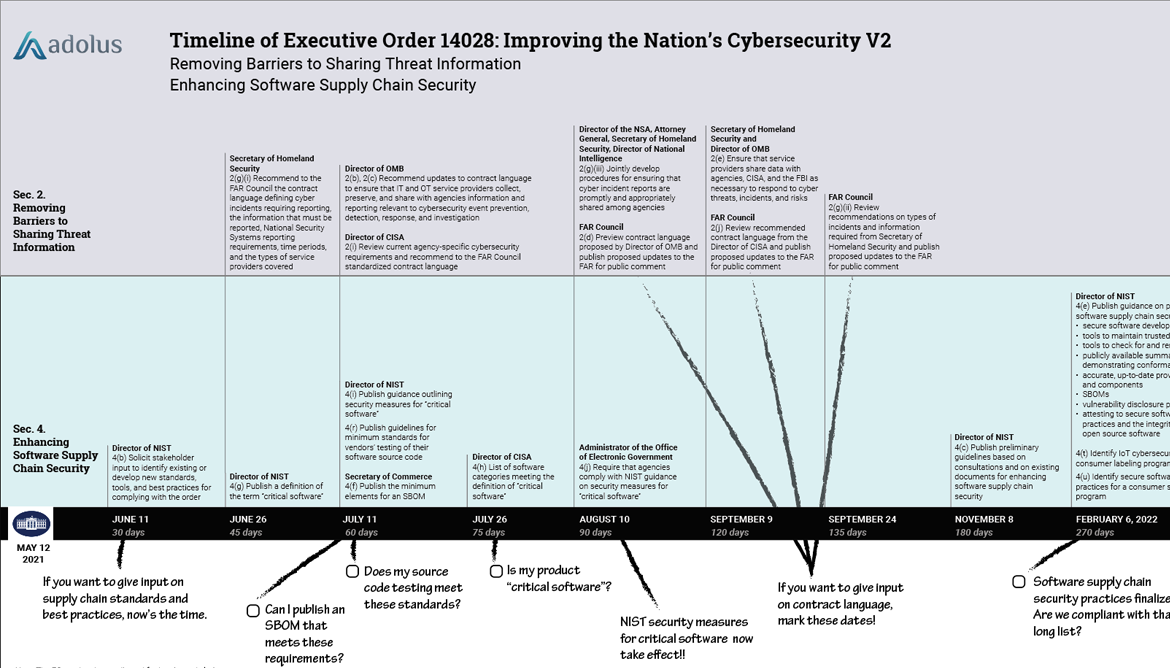
Removing Barriers to Sharing Threat Information On Friday we dissected Section 4: Enhancing Software Supply Chain Security of the new Executive Order on Improving the Nation’s Cybersecurity...
Continue ReadingUnpacking EO14028: Improving the Nation's Cybersecurity - Pt. 1
Late Wednesday night President Biden signed the Executive Order on Improving the Nation’s Cybersecurity. Compared to any Executive Order (EO) I’ve seen, this is a massive and complex...
Continue ReadingWrapping Up 2020 with Dale Peterson
Wrapping up my year on December 31, I was delighted to join ICS cybersecurity luminary Dale Peterson for his December: ICS Security Month in Review episode of the Unsolicited Response...
Continue ReadingThree Things the SolarWinds Supply Chain Attack Can Teach Us
Just in case you missed it, a software supply chain attack on the US government and industries is consuming the waking hours of everyone involved in cyber security this week. The attack...
Continue ReadingStay up to date
Browse Posts
- May 2024
- February 2024
- December 2023
- October 2023
- April 2023
- March 2023
- February 2023
- October 2022
- April 2022
- February 2022
- December 2021
- November 2021
- August 2021
- July 2021
- June 2021
- May 2021
- February 2021
- January 2021
- December 2020
- September 2020
- August 2020
- July 2020
- May 2020
- April 2020
- January 2020
- October 2019
- September 2019
- November 2018
- September 2018
- May 2018
Browse by topics
- Supply Chain Management (16)
- SBOM (15)
- Vulnerability Tracking (15)
- #supplychainsecurity (10)
- Regulatory Requirements (10)
- VEX (8)
- EO14028 (6)
- ICS/IoT Upgrade Management (6)
- malware (6)
- ICS (5)
- vulnerability disclosure (5)
- 3rd Party Components (4)
- Partnership (4)
- Press-release (4)
- #S4 (3)
- Software Validation (3)
- hacking (3)
- industrial control system (3)
- Code Signing (2)
- Legislation (2)
- chain of trust (2)
- #nvbc2020 (1)
- DoD CMMC (1)
- Dragonfly (1)
- Havex (1)
- Log4Shell (1)
- Log4j (1)
- Trojan (1)
- USB (1)
- Uncategorized (1)
- energy (1)
- medical (1)
- password strength (1)
- pharmaceutical (1)
Sidebar