- Blog
- /
- Topic
Malware
- All
- Supply Chain Management
- SBOM
- Vulnerability Tracking
- #supplychainsecurity
- Regulatory Requirements
- VEX
- EO14028
- ICS/IoT Upgrade Management
- malware
- ICS
- vulnerability disclosure
- 3rd Party Components
- Partnership
- Press-release
- #S4
- Software Validation
- hacking
- industrial control system
- Code Signing
- Legislation
- chain of trust
- #nvbc2020
- DoD CMMC
- Dragonfly
- Havex
- Log4Shell
- Log4j
- Trojan
- USB
- Uncategorized
- energy
- medical
- password strength
- pharmaceutical
Harnessing FACT for Swift Cyberthreat Response
In the cybersecurity world, anticipation and rapid response are crucial in safeguarding against emerging threats. Recent events, such as the discovery of a vulnerability in the XZ Utils...
Continue ReadingDon’t Judge an Ebook by Its Cover
Interesting times lead to interesting opportunities. The current pandemic is proving no exception, but, sadly, it’s an opportunity for some attackers who have laid a rather cunning trap. As...
Continue ReadingSniffing Out Fakes: From Saffron in Marrakech to Digital Certificates
Eric Byres in Morocco
Continue ReadingWhen the Security Researchers Come Knocking, Don’t Shoot the Messenger
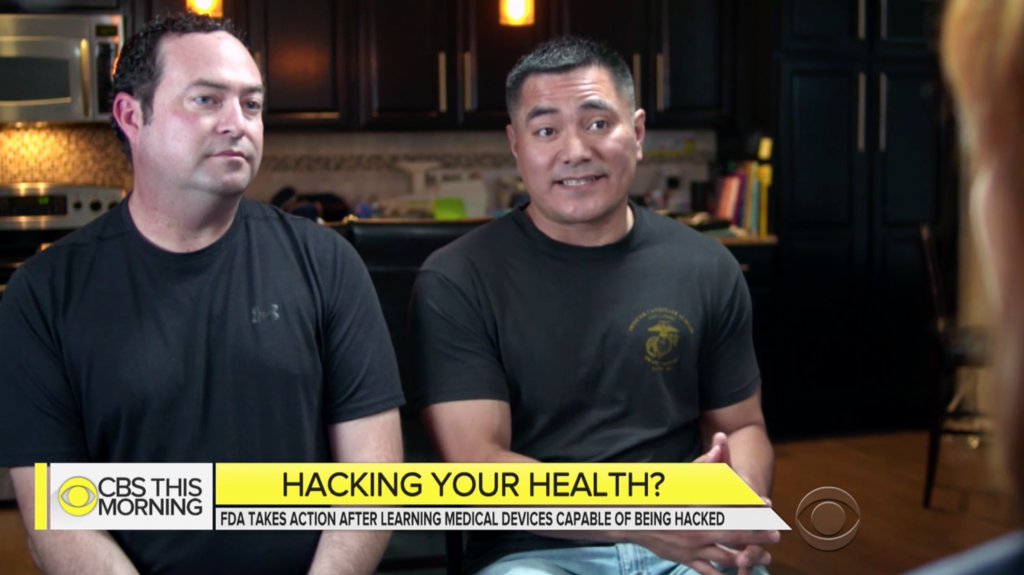
Our own Jonathan Butts and Billy Rios were interviewed this month on the CBS Morning News about their research showing that medical devices like pacemakers and insulin pumps can be hacked...
Continue ReadingWho Infected Schneider Electrics’ Thumbdrive?
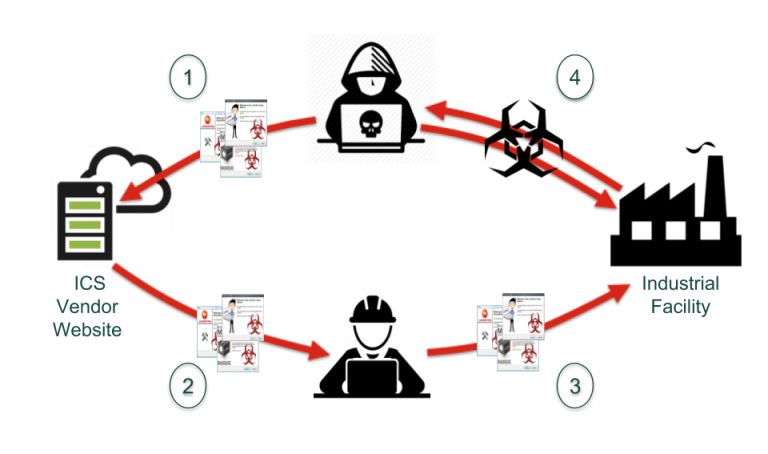
On 24 August 2018 Schneider Electric issued a security notification alerting users that the Communications and Battery Monitoring devices for their Conext Solar Energy Monitoring Systems...
Continue ReadingBuilding (or Losing) Trust in our Software Supply Chain
Back in 2014, when I was managing Tofino Security, I became very interested in the Dragonfly attacks against industrial control systems (ICS). I was particularly fascinated with the ways...
Continue ReadingStay up to date
Browse Posts
- May 2024
- February 2024
- December 2023
- October 2023
- April 2023
- March 2023
- February 2023
- October 2022
- April 2022
- February 2022
- December 2021
- November 2021
- August 2021
- July 2021
- June 2021
- May 2021
- February 2021
- January 2021
- December 2020
- September 2020
- August 2020
- July 2020
- May 2020
- April 2020
- January 2020
- October 2019
- September 2019
- November 2018
- September 2018
- May 2018
Browse by topics
- Supply Chain Management (16)
- SBOM (15)
- Vulnerability Tracking (15)
- #supplychainsecurity (10)
- Regulatory Requirements (10)
- VEX (8)
- EO14028 (6)
- ICS/IoT Upgrade Management (6)
- malware (6)
- ICS (5)
- vulnerability disclosure (5)
- 3rd Party Components (4)
- Partnership (4)
- Press-release (4)
- #S4 (3)
- Software Validation (3)
- hacking (3)
- industrial control system (3)
- Code Signing (2)
- Legislation (2)
- chain of trust (2)
- #nvbc2020 (1)
- DoD CMMC (1)
- Dragonfly (1)
- Havex (1)
- Log4Shell (1)
- Log4j (1)
- Trojan (1)
- USB (1)
- Uncategorized (1)
- energy (1)
- medical (1)
- password strength (1)
- pharmaceutical (1)
Sidebar