Removing Barriers to Sharing Threat Information
On Friday we dissected Section 4: Enhancing Software Supply Chain Security of the new Executive Order on Improving the Nation’s Cybersecurity. Today we will look at Section 2: Removing Barriers to Sharing Threat Information. We’ve also updated the EO14028 Timeline I posted previously to include Section 2 deadlines:
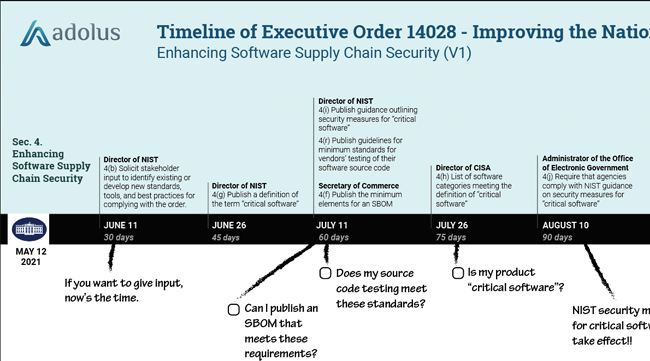
 |
Timeline of Executive Order 14028: Improving the Nation’s Cybersecurity Removing Barriers to Sharing Threat Information (V2) |
The EO Fact Sheet makes the goal of Section 2 clear:
Removing any contractual barriers and requiring providers to share breach information that could impact Government networks...
Sure enough, the 13 directives spread over 3 pages point to a single main objective: to make certain that all US government contracts require service providers to collect and share cyber event information with US agencies.
Specifically, Section 2 calls for a review and update of the Federal Acquisition Regulation (FAR) and Defense Federal Acquisitions Regulation Supplement (DFARS) to ensure that service providers:
- Collect and preserve information relevant to cybersecurity event prevention, detection, response, and investigation.
- Share the cyber information with the agencies determined by the government.
- Share the cyber information using industry-recognized formats.
- Collaborate with Federal cybersecurity and investigative agencies as needed.
In case anyone was wondering, the information sharing is 100% unidirectional flow from private industry to the government (a data-diode anyone?). There’s no mention of removing the barriers that prevent the government from sharing threat intelligence with operators of critical infrastructures. That is a pity because I’ve been in situations when a little government threat-intel would have significantly improved a security team’s ability (and management’s motivation) to defend an OT system from cyber attack. Oh well….
Who will be impacted by these changes to government contracts? At first glance I thought it was just the IT companies who provide contract services to the federal government. Then I reread the first line of the section:
The Federal Government contracts with IT and OT service providers to conduct an array of day-to-day functions on Federal Information Systems.
It is not clear to me how an OT service provider might “conduct functions” on an IT system. Maybe it is keeping the electricity flowing to the server room. But OT companies are specifically called out and I’m sure that is intentional.
Perhaps this is a result of the Colonial Pipeline incident. On Tuesday, May 11, four days after that attack started, the acting Cybersecurity and Infrastructure Security Agency (CISA) Director Brandon Wales told the Senate Homeland Security Committee that the CISA was still waiting for Colonial Pipeline to share key data about the attack. Colonial didn’t even contact CISA after discovering the hack, Wales said. Instead, the company contacted the FBI, which then brought in CISA. I’m just guessing, but “OT” might have been added to Section 2 that Tuesday afternoon by a rather frustrated CISA leadership team.
Finally, when will service providers, be they IT or OT, have to comply with the new contracting agreements? That isn’t clear in the EO, but based on previous FAR rule change cycles, I’m guessing the period for public comments will close in late December 2021 and the FAR Final Rule will occur in late 2022. Contracts after that date will have to follow the new information sharing requirements.
Watch for more analysis of the EO on Thursday as we dig into Section 3: Modernizing Federal Government Cybersecurity. Until then, please comment below if you have any questions or suggestions regarding our analysis of the EO.
As always, if you are looking for guidance on improving the security of your software supply chain, please reach out.

Eric Byres
Eric is widely recognized as one of the world’s leading experts in the field of OT, IT and IoT software supply chain security. He is the inventor of the Tofino Security technology – the most widely deployed OT-specific firewall in the world. When not setting the product vision, or speaking at a conference, Eric can be found cranking away on his gravel bike.
Stay up to date
Browse Posts
- May 2024
- February 2024
- December 2023
- October 2023
- April 2023
- March 2023
- February 2023
- October 2022
- April 2022
- February 2022
- December 2021
- November 2021
- August 2021
- July 2021
- June 2021
- May 2021
- February 2021
- January 2021
- December 2020
- September 2020
- August 2020
- July 2020
- May 2020
- April 2020
- January 2020
- October 2019
- September 2019
- November 2018
- September 2018
- May 2018
Browse by topics
- Supply Chain Management (16)
- SBOM (15)
- Vulnerability Tracking (15)
- #supplychainsecurity (10)
- Regulatory Requirements (10)
- VEX (8)
- EO14028 (6)
- ICS/IoT Upgrade Management (6)
- malware (6)
- ICS (5)
- vulnerability disclosure (5)
- 3rd Party Components (4)
- Partnership (4)
- Press-release (4)
- #S4 (3)
- Software Validation (3)
- hacking (3)
- industrial control system (3)
- Code Signing (2)
- Legislation (2)
- chain of trust (2)
- #nvbc2020 (1)
- DoD CMMC (1)
- Dragonfly (1)
- Havex (1)
- Log4Shell (1)
- Log4j (1)
- Trojan (1)
- USB (1)
- Uncategorized (1)
- energy (1)
- medical (1)
- password strength (1)
- pharmaceutical (1)















Post a comment