Earlier this summer, aDolus collaborated with Microsoft on vulnerability analysis and contributed to their Microsoft Digital Defense Report 2023 (MDDR 2023). This report is a significant document and popular reading for heads of state and Davos regulars, so we were delighted when they approached us for our expertise.
You can read the summary of our joint research in the MDDR 2023, so in this blog I’ll take you behind the scenes and shed some light on the technology we used to provide Microsoft with the intelligence they were looking for. In my next blog I will provide my interpretation of the results and what they tell us about the state of patching in the OT world.
Behind the Scenes
Microsoft kicked off the project by using their extensive Defender for IoT customer base to build a list of the 1200 most commonly deployed OT (Operational Technology) devices. The initial list included a wide variety of devices, such as network hardware, drive controllers and Human Machine Interface (HMI) panels. We conducted analysis of all these devices, but in the end we jointly decided to focus the report on PLCs (programmable logic controllers). PLCs are the devices that monitor sensors and control actuators to manage industrial processes. They are a key component in our critical infrastructure, keeping manufacturing lines running, gas pipelines flowing, pharmaceutical products shipping, and much more.
For every device on the list, Microsoft provided the raw description of the asset group with vendor, model name and version discovered in the field. Any information like tag names that could reveal where these devices might be located or the companies using them was stripped out. Even the number of devices found in the field was removed from the data we received so full anonymity was maintained.
Overcoming the Mess of Names
Once we had the asset lists we ran them against our AI-based vulnerability search engines. We developed this capability to hunt for vulnerabilities associated with components found in SBOMs, but it turns out these search algorithms work just as well finding OT device vulnerabilities. In both cases our AI-engine first needs to address the “namespace problem” by developing an extensive list of aliases for relevant vendor and product names. For example, the National Vulnerability Database (NVD) indicates the Common Platform Enumeration or CPE (i.e. the searchable name for a vulnerable device) for one particular Siemen’s PLC is:
simatic_s7-300_with_profitnet_support_firmware
However, no OT asset list will contain a model name like that. Instead the asset lists will likely have some variation of the manufacturer’s common product identifiers, such as SIMATIC S7-300 CPU 315-2 PN/DP or S7-315-PN, or even a part number like 6ES7315-2EH14-0AB0. Similarly Profinet is often capitalized as either PROFINET or ProfiNet or abbreviated as PN in both vendor descriptions and asset databases.
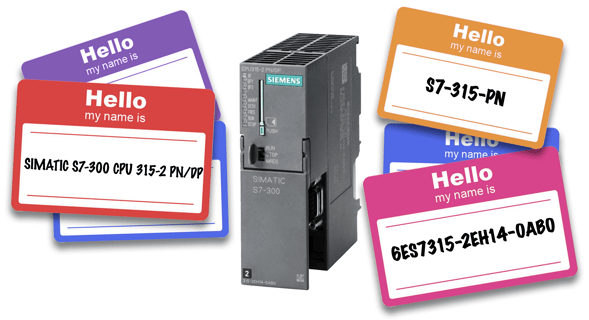 To solve this challenge, the AI system creates a hierarchy of common names and then uses variations of those aliases to hunt for matches in the various vulnerability databases. Often a vendor or product will have several hundred common variations of a name, including spelling mistakes and punctuation variations.
To solve this challenge, the AI system creates a hierarchy of common names and then uses variations of those aliases to hunt for matches in the various vulnerability databases. Often a vendor or product will have several hundred common variations of a name, including spelling mistakes and punctuation variations.
Searching the NVD Is Never Enough
The second phase of the intelligent search is to look beyond the NVD database and explore other vulnerability databases, such as CISA’s ICS-CERT Cybersecurity Alerts & Advisories or the various vendor databases. This is critical because research conducted by Kaspersky in 2019 showed that over 76% of OT vulnerabilities were never listed in the NVD.
The challenge is that most of these non-NVD databases contain only text-based advisory notices. There are no consistent search indexes, so our algorithms have to resort to Natural Language Processing of thousands of PDFs. Using machine learning, the text in each of these PDFs is tokenized into terms of interest and scored for importance for matching to specific products and versions.
The end result from running these processes against the Microsoft Most Common OT Assets list was a list of probable vulnerabilities mapped against each product and version. Some newer firmware versions had no published vulnerabilities against them, while some older versions had accumulated over a dozen reported vulnerabilities over the years.
The release dates for each version were also mapped so that we could easily show how old a given version was and how many patches had been released for it.
Frankly, even for an old OT hand like me, the results were a shock. In my next blog I’ll talk about what we learned from the joint analysis. (Spoiler alert, the title of the next blog is The Wretched State of OT Firmware Patching.)

Eric Byres
Eric is widely recognized as one of the world’s leading experts in the field of OT, IT and IoT software supply chain security. He is the inventor of the Tofino Security technology – the most widely deployed OT-specific firewall in the world. When not setting the product vision, or speaking at a conference, Eric can be found cranking away on his gravel bike.
Stay up to date
Browse Posts
- May 2024
- February 2024
- December 2023
- October 2023
- April 2023
- March 2023
- February 2023
- October 2022
- April 2022
- February 2022
- December 2021
- November 2021
- August 2021
- July 2021
- June 2021
- May 2021
- February 2021
- January 2021
- December 2020
- September 2020
- August 2020
- July 2020
- May 2020
- April 2020
- January 2020
- October 2019
- September 2019
- November 2018
- September 2018
- May 2018
Browse by topics
- Supply Chain Management (16)
- SBOM (15)
- Vulnerability Tracking (15)
- #supplychainsecurity (10)
- Regulatory Requirements (10)
- VEX (8)
- EO14028 (6)
- ICS/IoT Upgrade Management (6)
- malware (6)
- ICS (5)
- vulnerability disclosure (5)
- 3rd Party Components (4)
- Partnership (4)
- Press-release (4)
- #S4 (3)
- Software Validation (3)
- hacking (3)
- industrial control system (3)
- Code Signing (2)
- Legislation (2)
- chain of trust (2)
- #nvbc2020 (1)
- DoD CMMC (1)
- Dragonfly (1)
- Havex (1)
- Log4Shell (1)
- Log4j (1)
- Trojan (1)
- USB (1)
- Uncategorized (1)
- energy (1)
- medical (1)
- password strength (1)
- pharmaceutical (1)
















Post a comment