NOTE: We were going to publish our second blog of the S4x23 SBOM Challenge today. However, the new National Cybersecurity Strategy was released this morning, and we thought that dissecting it for our readers took priority. We’ll go back to the S4x23 SBOM Challenge discussion next week.
There is a lot to unpack and there is even more to read between lines in the Biden Administration's new National Cybersecurity Strategy. Let me lay out the three things that stood out on my first read.
-
The real threat: The Biden administration is acknowledging that the real cybersecurity threat is from hostile nations and not your average cybercriminal. While attacks from cybercriminals are common in everyday news, skilled actors operating out of foreign intelligence agencies will be responsible for any big disasters, especially against our critical infrastructures. Two-thirds of the section titled Malicious Actors (page 3) focuses on calling out China, Russia, Iran, and North Korea as the sponsors of the most damaging cyber attacks of the past five years. The gloves are off and the US government is now setting its sights on defending the nation from the true threat.
-
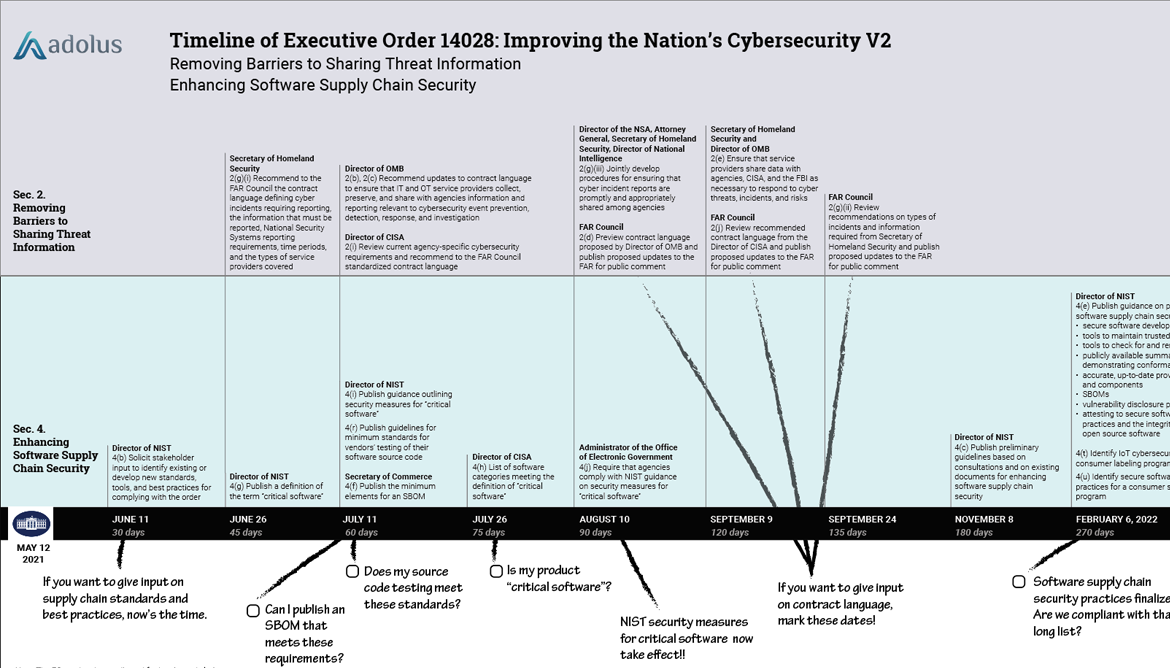
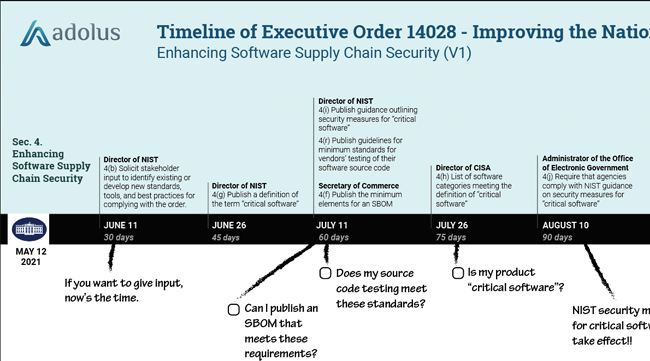
OT security is finally getting the attention it deserves: While the attention started with EO14028, the government is now recognizing that OT is not the same as IT (or IoT) and protecting these systems is critical to the well-being of the western world. And they understand that many of the OT systems deployed today will need to be replaced — on page 13 the document notes:
The Federal Government must replace or update IT and OT systems that are not defensible against sophisticated cyber threats.
The section goes on to say:
The plan will identify milestones to remove all legacy systems incapable of implementing our zero trust architecture strategy within a decade.
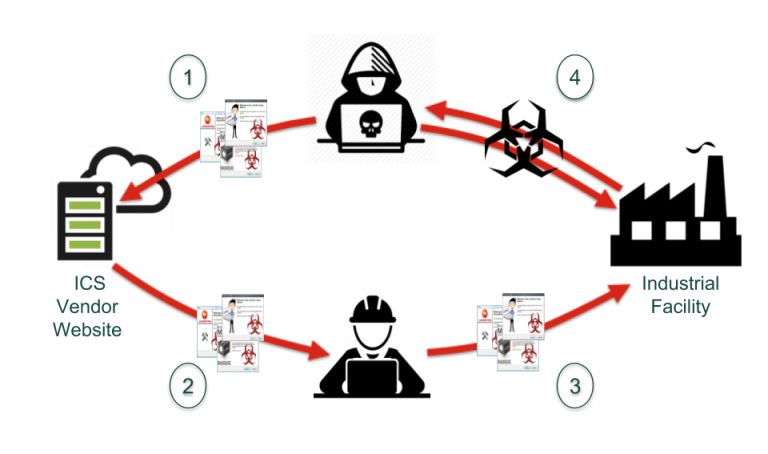
Now for the moment, this applies only to federal systems, but — as has become blindingly obvious — any rules laid out for federal agencies will apply to the public sector in short order. What's this going to mean for all the legacy equipment out there in industrial environments cheerfully communicating over Modbus?
- More regulation is coming: The strategy recognizes that
…market forces alone have not been enough to drive broad adoption of best practices in cybersecurity and resilience.
Regulations and changes in liability law will be used to encourage technology providers, especially for critical infrastructure, to do the right thing. Taking shortcuts and embedding 3rd-party code of questionable provenance into products is going to have consequences.
At the same time, the government wants to help those companies that do try to ship a secure product:
…the Administration will drive the development of an adaptable safe harbor framework to shield from liability companies that securely develop and maintain their software products and services.
In addition to drawing from
current best practices for secure software development, such as the NIST Secure Software Development Framework,
the strategy calls for this safe harbor to
evolve over time, incorporating new tools for secure software development, software transparency, and vulnerability discovery.
Increasing transparency and building trust in our industry has been the goal of aDolus since its formation in 2017. I believe that FACT can help companies secure moorage in this "safe harbor” by providing software transparency and vulnerability discovery at scale.

Eric Byres
Eric is widely recognized as one of the world’s leading experts in the field of OT, IT and IoT software supply chain security. He is the inventor of the Tofino Security technology – the most widely deployed OT-specific firewall in the world. When not setting the product vision, or speaking at a conference, Eric can be found cranking away on his gravel bike.
Stay up to date
Browse Posts
- May 2024
- February 2024
- December 2023
- October 2023
- April 2023
- March 2023
- February 2023
- October 2022
- April 2022
- February 2022
- December 2021
- November 2021
- August 2021
- July 2021
- June 2021
- May 2021
- February 2021
- January 2021
- December 2020
- September 2020
- August 2020
- July 2020
- May 2020
- April 2020
- January 2020
- October 2019
- September 2019
- November 2018
- September 2018
- May 2018
Browse by topics
- Supply Chain Management (16)
- SBOM (15)
- Vulnerability Tracking (15)
- #supplychainsecurity (10)
- Regulatory Requirements (10)
- VEX (8)
- EO14028 (6)
- ICS/IoT Upgrade Management (6)
- malware (6)
- ICS (5)
- vulnerability disclosure (5)
- 3rd Party Components (4)
- Partnership (4)
- Press-release (4)
- #S4 (3)
- Software Validation (3)
- hacking (3)
- industrial control system (3)
- Code Signing (2)
- Legislation (2)
- chain of trust (2)
- #nvbc2020 (1)
- DoD CMMC (1)
- Dragonfly (1)
- Havex (1)
- Log4Shell (1)
- Log4j (1)
- Trojan (1)
- USB (1)
- Uncategorized (1)
- energy (1)
- medical (1)
- password strength (1)
- pharmaceutical (1)













Post a comment