Section 3 - Less Fog, More Cloud
Section 3: Modernizing Federal Government Cybersecurity of the Executive Order is all about government agencies moving to the cloud and doing it right. If you are someone who believes that the cloud has absolutely no place in the industrial control systems (ICS) world, you are going to hate this section.
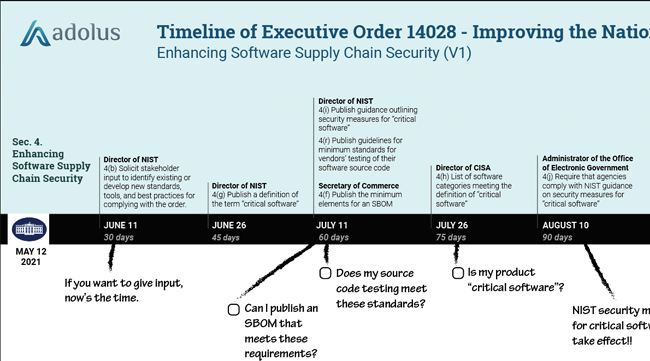
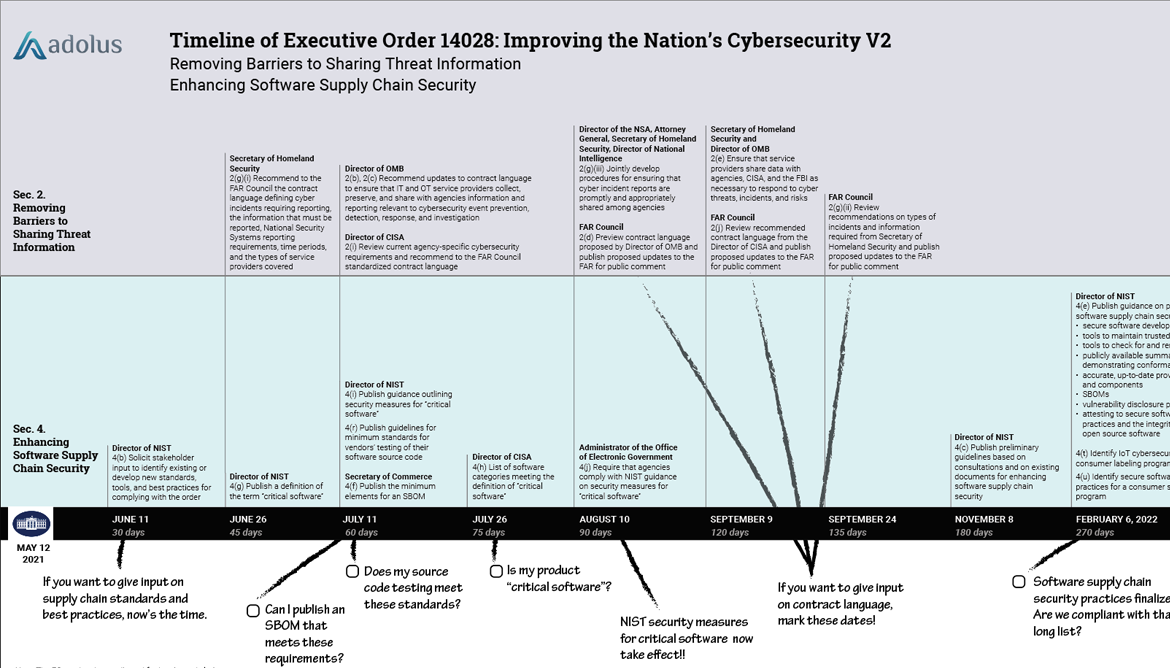
| The aDolus team has converted our previous EO Timeline to a web page that more easily handles all the sections and associated dates & deadlines. Bookmark it and stay on top of the EO! |

|
The section starts with a preamble;
The Federal Government must take decisive steps to modernize its approach to cybersecurity.
Then the section goes on to say that the government will accelerate movement to cloud technologies and there will be a single coordinated approach for cloud security strategies and service purchases by government agencies.
The government’s cloud service security strategy has needed modernization for a while now. It has been over a decade since the US Government started moving its data storage away from agency-owned data centers and towards using cloud-based services. Unfortunately, despite good intentions, the government's requirements for cloud security have been rather “foggy” to say the least. For example, the Office of Management and Budget released its Cloud Smart Strategy in 2019 to help agencies securely migrate to the cloud. While security was one of the three pillars of that report, the guidance was largely a collection of security truisms like
This requires that agencies place an emphasis on… transitioning to a multi-layer defense strategy, otherwise known as defense-in-depth.
Use defence-in-depth… wow, what a radical idea.
The EO aims to modernize the US government’s cloud security posture in four ways. The first directs CISA to develop secure cloud adoption practices and guidelines, offer incident response services to government cloud users, and set policy on how agencies should work with partners like CISA and the FBI in responding to cloud incidents. The timeline to develop these complex policies is tight, 90 days or less in each case.
The second set of clauses is a requirement for all agencies to implement a Zero Trust Architecture for all cloud computing services. If you are not familiar with Zero Trust Architecture (and frankly it isn't often discussed in the OT world), you need to jump ahead to Sec. 10. Definitions. The EO’s definition begins:
a security model… based on an acknowledgement that threats exist both inside and outside traditional network boundaries.
In other words, you assume the bad guys are already inside your network and now you need to manage them.
Zero Trust (sometimes called perimeterless security) has been discussed in the IT world since the 1990s. My good friend Paul Dorey, tried to bring it to the OT world in the early 2000’s when he was the CSO at BP. Unfortunately the concept of Zero Trust was and still is an anathema to many in the OT world. For the past 30 years the design of industrial control systems has been based on the dubious assumption that everything connected to the ICS network is friendly. As Dale Peterson says, that traditional OT security strategy should be called Insecure-by-Design. Frankly, I agree.
PaloAlto Networks has a good, quick summary of the Zero Trust philosophy if you want more details. But it’s the next sentence in the EO definition that stood out to me:
The Zero Trust security model eliminates implicit trust in any one element, node, or service and instead requires continuous verification of the operational picture via real-time information from multiple sources to determine access and other system responses.
“Continuous” verification is no trivial task. Anyone who has tried to determine if their ICS software contains vulnerabilities will know that new vulnerabilities are found all the time, and they can be hidden in components you don’t even know you’ve got. Also, monitoring “real-time information from multiple sources” isn’t the kind of job that humans excel at. Satisfying this requirement in the EO is going to require automation of trust validation.
Next, the order requires all agencies to adopt multi-factor authentication (MFA) and encryption for all data at rest and in transit. Note the phrase data at rest. Just deploying your PLC’s communications over SSL isn’t going to cut it.
If you are selling to the Feds (or to companies that will expect the same commitment to cybersecurity that the Feds are demanding) your software must implement MFA and data encryption. This isn’t a quick and simple retrofit for ICS; you’ll need to start early as you’ve only got 180 days to come up with a solution. And you’ll want to build this in from the get go for new software in the future. Of course there is an escape clause - agencies using products that are unable to comply must provide a written report explaining why they are unable to comply. That should be a fun pile of paperwork to fill out.
Finally, the Administrator of General Services is tasked with a significant set of actions to modernize FedRAMP (the federal government’s main security authorization program for cloud services) by July 11. There is significant emphasis here on more-automated, more-rapid and less-duplicative reviews of new cloud services:
improving communication with CSPs (Cloud Service Providers) through automation and standardization of messages at each stage of authorization. These communications may include status updates, requirements to complete a vendor’s current stage, next steps, and points of contact for questions
It is encouraging to see acknowledgement that automation will be necessary.
So what has any of this cloud stuff got to do with OT you ask? Well, every one of the major automation vendors is now promoting a significant cloud services solution for tasks like asset management, process optimization, and security response coordination. Sure you don’t have to use those cloud services, but customers soon find that they lose some very useful capabilities when they do that. So while closed-loop control over the cloud might be a ways off yet, control system communication to the cloud is here now.
To Close...
It is clear that cloud technology is going to be a big area of attention for this administration. Companies with secure and robust cloud security solutions will be the beneficiaries. On the other hand, if your company supplies a product that doesn’t support multi-factor authentication and encryption of data both in transit and at rest, you and your government clients may have a lot of paperwork to do in the next 180 days.
As always, if you want to be notified of the next report on EO14028, click Subscribe (down to the right).

Eric Byres
Eric is widely recognized as one of the world’s leading experts in the field of OT, IT and IoT software supply chain security. He is the inventor of the Tofino Security technology – the most widely deployed OT-specific firewall in the world. When not setting the product vision, or speaking at a conference, Eric can be found cranking away on his gravel bike.
Stay up to date
Browse Posts
- May 2024
- February 2024
- December 2023
- October 2023
- April 2023
- March 2023
- February 2023
- October 2022
- April 2022
- February 2022
- December 2021
- November 2021
- August 2021
- July 2021
- June 2021
- May 2021
- February 2021
- January 2021
- December 2020
- September 2020
- August 2020
- July 2020
- May 2020
- April 2020
- January 2020
- October 2019
- September 2019
- November 2018
- September 2018
- May 2018
Browse by topics
- Supply Chain Management (16)
- SBOM (15)
- Vulnerability Tracking (15)
- #supplychainsecurity (10)
- Regulatory Requirements (10)
- VEX (8)
- EO14028 (6)
- ICS/IoT Upgrade Management (6)
- malware (6)
- ICS (5)
- vulnerability disclosure (5)
- 3rd Party Components (4)
- Partnership (4)
- Press-release (4)
- #S4 (3)
- Software Validation (3)
- hacking (3)
- industrial control system (3)
- Code Signing (2)
- Legislation (2)
- chain of trust (2)
- #nvbc2020 (1)
- DoD CMMC (1)
- Dragonfly (1)
- Havex (1)
- Log4Shell (1)
- Log4j (1)
- Trojan (1)
- USB (1)
- Uncategorized (1)
- energy (1)
- medical (1)
- password strength (1)
- pharmaceutical (1)














Post a comment