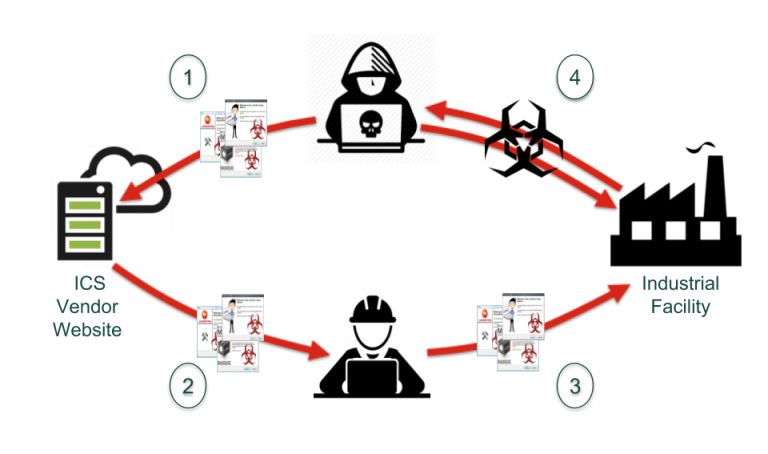
Interesting times lead to interesting opportunities. The current pandemic is proving no exception, but, sadly, it’s an opportunity for some attackers who have laid a rather cunning trap. As you no doubt know, supply chain security typically focuses on firmware and installers. However, in the course of researching vendor documentation, we saw a clever technique being utilized by attackers targeting critical infrastructure and industrial asset owners.
Instead of modifying software, the bad guys are going after ICS documentation. They are planting modified documents using legitimate titles and content from OEM manuals, thus polluting search engine results so that they can deliver a modified PDF/drive-by download to potentially compromise ICS systems. What we observed began about 2 weeks ago and it’s been getting worse since then.
Why is this scheme clever?
- It targets specific industries susceptible to already known vulnerabilities.
- It mimics real content on Google by stealing legitimate hosting on a valid domain, such as a university.
- It blends in with system integrators hosting various information and installers outside of the official OEM ecosystem.
- It targets end users who might not be the most cyber-savvy, especially if they are in a hurry or struggling during this pandemic.
In case you still think air gaps are a thing, this type of attack ends that debate. Any well-meaning technician seeking a manual or other deployment document, or perhaps an application installer, can download what they believe is a legitimate file right into their facility — bypassing the facility’s “secure” perimeter. The Google search results look reasonable enough, and that may seem like a faster way to get your hands on a document than navigating through a complex vendor website.
Let me share an example. On our hunt for the manual for an Emerson Delta-V DCS, we ran into a downright weird site that seemed pretty sketchy (not to pick on Emerson: we ran into variants of this issue with other vendors as well). Googling for the manual returned results that looked fairly reasonable:
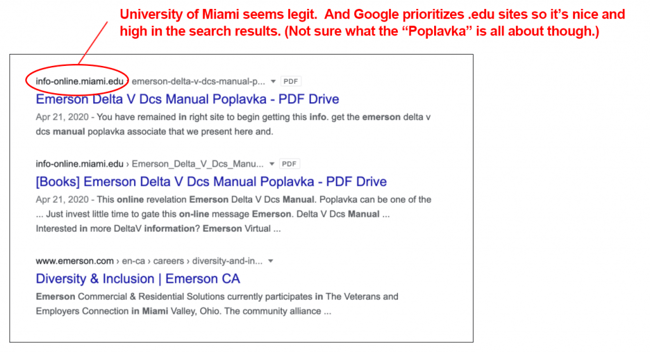
We went ahead and clicked the first result (as one might do if they are in a hurry, had trouble tracking down the manual via other searches, or just generally consider .edu sites to be trustworthy). We then found ourselves here:
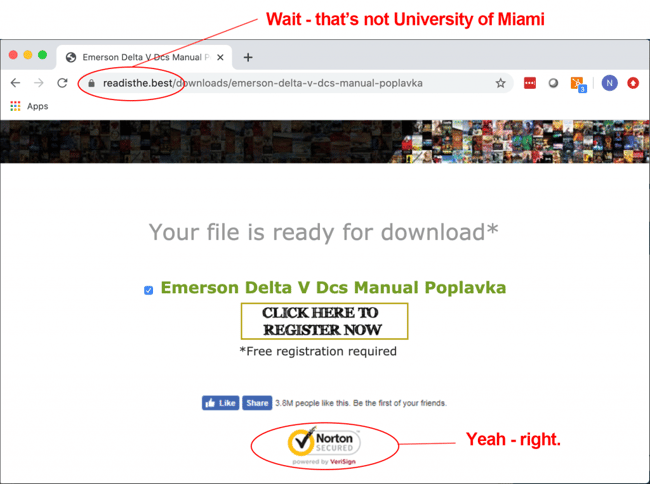
Suspicious, we checked out that original domain info-online.miami.edu from the Google results and something definitely looked strange (and each time we reloaded the page, the list of seemingly random titles was different):
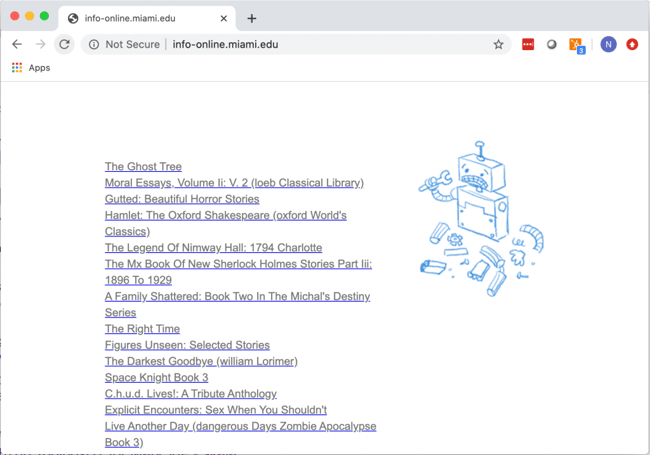
No way were we going to click on that ![]() link.
link.
We had a similar experience when Googling for a GE training manual. (I won’t bother with all the screen captures from that adventure!) The manual showed up in the results multiple times, using the exact text and product names from the authentic GE document — but they were hosted on a bunch of .ru sites. And a comparison of one of the Russian versions and the real document showed that the PDF had indeed been tampered with. The XML in the PDF had been rewritten and the trailer (tail end) was removed. We haven’t yet done a full analysis on the details of the tampering, but you obviously don’t want technicians downloading it onto a secure plant floor.
Most OT sites are soft targets on the inside, so the impacts could be highly disruptive (e.g., delivery of ransomware) and the infected user instantly becomes an unwitting malware delivery service.
So what to do?
- For vendors: use FACT () to fingerprint your files, including your PDFs, and encourage your customers to always validate the origins of their software and to use your OEM portal.
- For asset owners: use FACT and authenticate files before letting them anywhere near your critical systems.
- For everyone: perform endpoint protection to block commodity malware and limit unauthorized software or documentation from being installed.
FACT is free (and easy) to use, so there’s really no reason to take risks with files of dubious origin. Try out FACT here.
Stay up to date
Browse Posts
- May 2024
- February 2024
- December 2023
- October 2023
- April 2023
- March 2023
- February 2023
- October 2022
- April 2022
- February 2022
- December 2021
- November 2021
- August 2021
- July 2021
- June 2021
- May 2021
- February 2021
- January 2021
- December 2020
- September 2020
- August 2020
- July 2020
- May 2020
- April 2020
- January 2020
- October 2019
- September 2019
- November 2018
- September 2018
- May 2018
Browse by topics
- Supply Chain Management (16)
- SBOM (15)
- Vulnerability Tracking (15)
- #supplychainsecurity (10)
- Regulatory Requirements (10)
- VEX (8)
- EO14028 (6)
- ICS/IoT Upgrade Management (6)
- malware (6)
- ICS (5)
- vulnerability disclosure (5)
- 3rd Party Components (4)
- Partnership (4)
- Press-release (4)
- #S4 (3)
- Software Validation (3)
- hacking (3)
- industrial control system (3)
- Code Signing (2)
- Legislation (2)
- chain of trust (2)
- #nvbc2020 (1)
- DoD CMMC (1)
- Dragonfly (1)
- Havex (1)
- Log4Shell (1)
- Log4j (1)
- Trojan (1)
- USB (1)
- Uncategorized (1)
- energy (1)
- medical (1)
- password strength (1)
- pharmaceutical (1)















Post a comment