Harnessing FACT for Swift Cyberthreat Response
In the cybersecurity world, anticipation and rapid response are crucial in safeguarding against emerging threats. Recent events, such as the discovery of a vulnerability in the XZ Utils...
Continue ReadingEvolving Threats and Regulations in Software Supply Chain Security
2023 is in the rearview mirror and 2024 is now well underway. I wanted to post my thoughts on some of the software supply chain trends we saw last year and how they will continue to shape...
Continue ReadingEU Cyber Resilience Act (CRA) Clears Penultimate Step
On December 3rd, the EU's new Cyber Resilience Act (CRA) got a big step closer to being adopted when the European Parliament and the EU Council reached an agreement on the legislation. It...
Continue ReadingThe Wretched State of OT Firmware Patching
This blog is a follow-up to our first post on the 2023 Microsoft Digital Defense Report where I described our collaboration with Microsoft on identified exploitable OT vulnerabilities.There...
Continue ReadingMicrosoft Digital Defense Report: Behind the Scenes Creating OT Vulnerabilities
Earlier this summer, aDolus collaborated with Microsoft on vulnerability analysis and contributed to their Microsoft Digital Defense Report 2023 (MDDR 2023). This report is a significant...
Continue ReadingAn Analysis of Generative AI: How to Be Confidently Wrong
The recent release of the National Cybersecurity Strategy document by the White House prompted me to test Microsoft's new Bing chat feature, which is powered by OpenAI's language model,...
Continue ReadingS4x23 SBOM Challenge — Part 3: VEX Document Ingestion
Three weeks ago I reported on the first part of the S4x23 SBOM Challenge run by Idaho National Laboratory (INL), which focused on SBOM Creation. Last week I reported on the second part:...
Continue ReadingS4x23 SBOM Challenge — Part 2: SBOM Ingestion
Two weeks ago I reported on the first part of the SBOM Challenge at the S4x23 cybersecurity conference in Miami, Florida. The Day 1 goal was for each team to create an accurate SBOM for...
Continue ReadingThree Quick Takeaways from Biden’s National Cybersecurity Strategy
NOTE: We were going to publish our second blog of the S4x23 SBOM Challenge today. However, the new National Cybersecurity Strategy was released this morning, and we thought that...
Continue ReadingS4x23 SBOM Challenge — Part 1
The aDolus Team has just returned from participating in the SBOM Challenge at the S4x23 cybersecurity conference in Miami, Florida. This blog is the first of a series reporting on what we...
Continue ReadingA Flurry of Regulatory Action and the Need for SBOMs
Executive Order 14028 on Improving the Nation's Cybersecurity was issued in May of 2021 and provided a roadmap for a series of regulatory initiatives that government agencies (and anyone...
Continue ReadingA Deeper Dive into VEX Documents
At the end of last summer, I wrote a blog post explaining the merits of Vulnerability Exploitability eXchange (VEX) documents. Almost 8 months later, I stand by the importance of these...
Continue ReadingHow Russia Might Come After the West
The DDoS attack surge that began last week against Ukrainian government agencies and banks was a bad sign. I was actually preparing a post and wondering if it was appropriate to call out...
Continue ReadingLog4j: Panic or Lesson? | How to Protect Deployed Assets
Cleaning up the Mess will Take a Methodical Approach Nearly every week the cybersecurity community buzzes around a newly discovered vulnerability or a breach. December’s alert for the ...
Continue ReadingSorry Blackberry: You Are Part of the Supply Chain
Today, reporters Betsy Woodruff Swan and Eric Geller at Politico published a story: “BlackBerry resisted announcing major flaw in software powering cars, hospital equipment.” They outline...
Continue ReadingWhat is VEX and What Does it Have to Do with SBOMs?
Recently, we have been fielding many inquiries here at aDolus regarding “VEX.” If you are not familiar with this mysterious abbreviation, you’ve fortunately landed in the right place....
Continue ReadingNTIA Publishes Minimum Components of an SBOM
In today’s blog post I’d like to recognize all the hard work done by NTIA (National Telecommunications and Information Administration) and congratulate them on publishing the minimum...
Continue ReadingKaseya Supply Chain Attack on SMBs
Last week I participated in a panel discussion on the Executive Order’s Impact On Embedded Device Security hosted by ISSSource.com. I signed off with a comment about my biggest worry: ...
Continue ReadingaDolus Welcomes Mark Weatherford to Board
Cybersecurity veteran tapped to accelerate growth of ICS supply chain security leader VICTORIA, BC, CANADA, June 23 -- aDolus Technology Inc., a global authority on software intelligence...
Continue ReadingRod Campbell Joins aDolus as CEO
Seasoned financial and advisory executive to drive growth VICTORIA, BC, CANADA, June 15, 2021 /EINPresswire.com/ -- aDolus Technology Inc., a global authority on software intelligence for...
Continue ReadingUnpacking EO14028: Improving the Nation's Cybersecurity - Pt. 4
Section 3 - Less Fog, More Cloud Section 3: Modernizing Federal Government Cybersecurity of the Executive Order is all about government agencies moving to the cloud and doing it right. If...
Continue ReadingUnpacking EO14028: Improving the Nation's Cybersecurity - Pt. 3
So you don’t sell to the Feds… Today’s blog is going to take a break from analyzing a specific section of the Executive Order on Improving the Nation’s Cybersecurity and focus on who will...
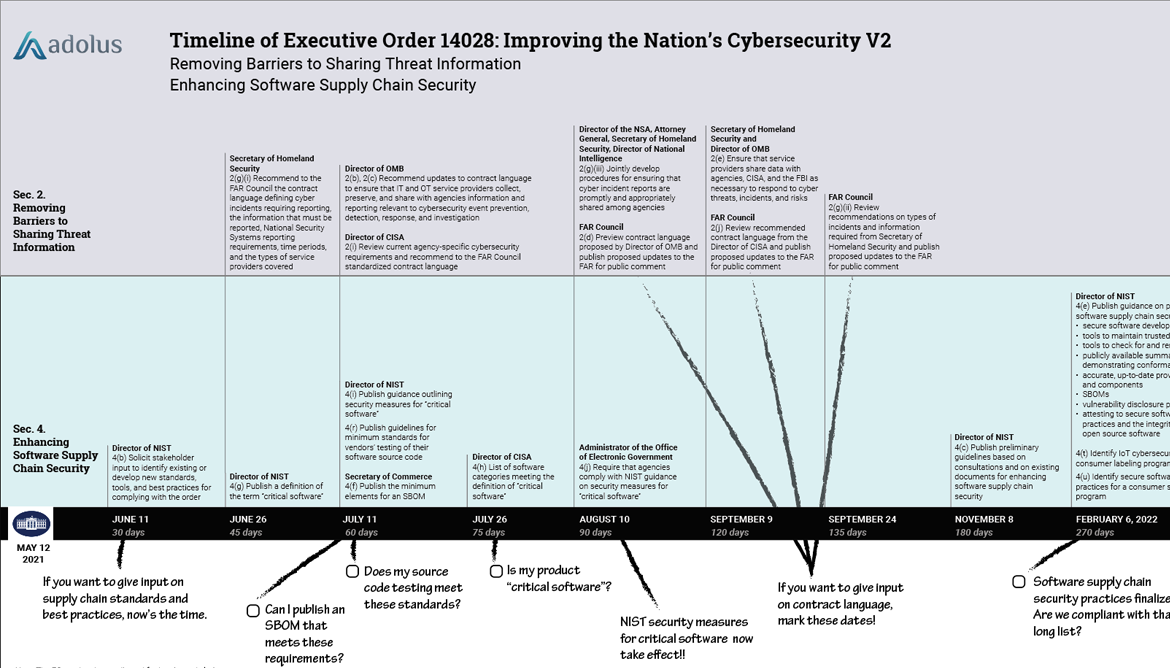
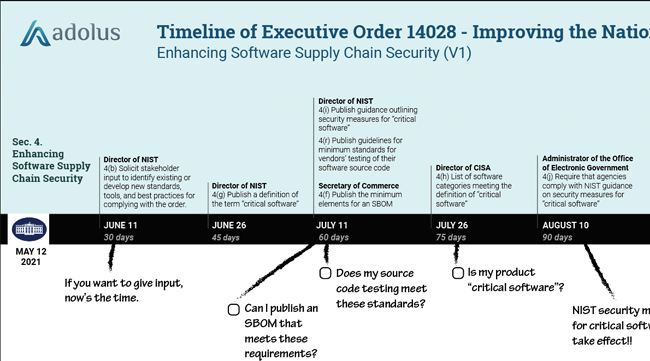
Continue ReadingUnpacking EO14028: Improving the Nation's Cybersecurity - Pt. 2
Removing Barriers to Sharing Threat Information On Friday we dissected Section 4: Enhancing Software Supply Chain Security of the new Executive Order on Improving the Nation’s Cybersecurity...
Continue ReadingUnpacking EO14028: Improving the Nation's Cybersecurity - Pt. 1
Late Wednesday night President Biden signed the Executive Order on Improving the Nation’s Cybersecurity. Compared to any Executive Order (EO) I’ve seen, this is a massive and complex...
Continue ReadingVerve Industrial and aDolus Partner to Reduce ICS Software Supply Chain Risk
Verve embeds aDolus’ ability to generate SBOMs and validate components aDolus Technology Inc., a global authority on software intelligence for critical infrastructure, today announced its...
Continue ReadingIndustrial Defender and aDolus Partner to Improve ICS Supply Chain Security
Industrial Defender’s integration with the aDolus FACT™ platform ensures updates are valid, tamper-free, and safe to install aDolus Technology Inc., a global authority on software...
Continue ReadingWrapping Up 2020 with Dale Peterson
Wrapping up my year on December 31, I was delighted to join ICS cybersecurity luminary Dale Peterson for his December: ICS Security Month in Review episode of the Unsolicited Response...
Continue ReadingThree Things the SolarWinds Supply Chain Attack Can Teach Us
Just in case you missed it, a software supply chain attack on the US government and industries is consuming the waking hours of everyone involved in cyber security this week. The attack...
Continue ReadingaDolus Wins Top Tech Innovation Contest, New Ventures BC 2020
aDolus Technology Inc. bested 240 of BC’s most innovative tech startups, winning the New Ventures contest in Canada’s #1 startup ecosystem, boasting over 10,000 tech companies. aDolus...
Continue ReadingReFirm Labs and aDolus Partner to Improve IoT Supply Chain Security
aDolus Technology Inc., a global authority on software intelligence for critical infrastructure, and ReFirm Labs, a provider of the industry’s first proactive IoT and firmware security...
Continue ReadingaDolus Technology Selected as One of 2020’s Top 10 Startups
NANAIMO, BC, CANADA, August 27, 2020: aDolus Technology Inc., a global authority on software intelligence for critical infrastructure, has today announced that New Ventures BC has selected...
Continue ReadingBayshore Networks and aDolus Forge Supply Chain Security Partnership
The aDolus FACT™ platform provides independent software update validation to ensure safe upgrades and a more secure supply chain NANAIMO, BC, CANADA, July 22, 2020 --aDolus Technology Inc.
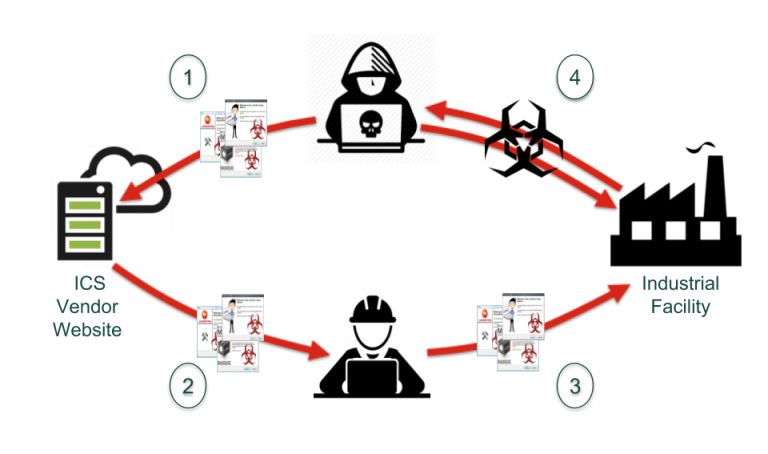
Continue ReadingDon’t Judge an Ebook by Its Cover
Interesting times lead to interesting opportunities. The current pandemic is proving no exception, but, sadly, it’s an opportunity for some attackers who have laid a rather cunning trap. As...
Continue Reading3 Month Reprieve for Utilities on Cybersecurity Supply Chain Standards
Earlier this month, as the coronavirus accelerated its alarming sprint across North America, NERC requested that FERC defer a number of looming deadlines for Reliability Standards....
Continue ReadingWindows 10 Certificate Validation Bug Exposes a Fundamental Weakness
The announcement Tuesday from the NSA about the new cryptographic vulnerability in the Microsoft Windows operating system sent ripples of shock through our entire community. In case you...
Continue ReadingSniffing Out Fakes: From Saffron in Marrakech to Digital Certificates
Eric Byres in Morocco
Continue ReadingPodcast: Where Do Your Bits Really Come From?
Earlier this year I attended the Public Safety Canada Industrial Control System Security symposium in Charlottetown, PEI (FYI the PSC ICS events are outstanding - worth attending, even if...
Continue ReadingWill the DoD’s CMMC Encourage Bad Password Habits?
Last Wednesday (September 11), the U.S. Department of Defense released a draft of its Cybersecurity Maturity Model Certification (CMMC) for public comment. The idea is for the DoD to...
Continue ReadingWhen the Security Researchers Come Knocking, Don’t Shoot the Messenger
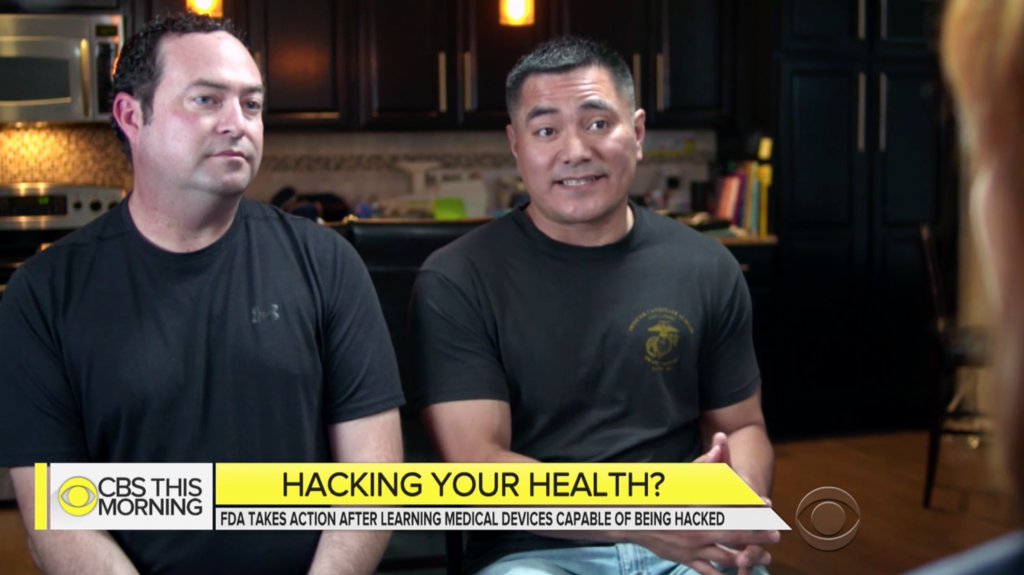
Our own Jonathan Butts and Billy Rios were interviewed this month on the CBS Morning News about their research showing that medical devices like pacemakers and insulin pumps can be hacked...
Continue ReadingWho Infected Schneider Electrics’ Thumbdrive?
On 24 August 2018 Schneider Electric issued a security notification alerting users that the Communications and Battery Monitoring devices for their Conext Solar Energy Monitoring Systems...
Continue ReadingBuilding (or Losing) Trust in our Software Supply Chain
Back in 2014, when I was managing Tofino Security, I became very interested in the Dragonfly attacks against industrial control systems (ICS). I was particularly fascinated with the ways...
Continue ReadingStay up to date
Browse Posts
- May 2024
- February 2024
- December 2023
- October 2023
- April 2023
- March 2023
- February 2023
- October 2022
- April 2022
- February 2022
- December 2021
- November 2021
- August 2021
- July 2021
- June 2021
- May 2021
- February 2021
- January 2021
- December 2020
- September 2020
- August 2020
- July 2020
- May 2020
- April 2020
- January 2020
- October 2019
- September 2019
- November 2018
- September 2018
- May 2018
Browse by topics
- Supply Chain Management (16)
- SBOM (15)
- Vulnerability Tracking (15)
- #supplychainsecurity (10)
- Regulatory Requirements (10)
- VEX (8)
- EO14028 (6)
- ICS/IoT Upgrade Management (6)
- malware (6)
- ICS (5)
- vulnerability disclosure (5)
- 3rd Party Components (4)
- Partnership (4)
- Press-release (4)
- #S4 (3)
- Software Validation (3)
- hacking (3)
- industrial control system (3)
- Code Signing (2)
- Legislation (2)
- chain of trust (2)
- #nvbc2020 (1)
- DoD CMMC (1)
- Dragonfly (1)
- Havex (1)
- Log4Shell (1)
- Log4j (1)
- Trojan (1)
- USB (1)
- Uncategorized (1)
- energy (1)
- medical (1)
- password strength (1)
- pharmaceutical (1)
Sidebar